 #WORDPRESS
#WORDPRESS Investigating a Compromised WordPress Site
Diagnosing a WordPress site compromise that was redirecting visitors to adult content and pharmaceutical spam through injected malicious scripts.
Read ArticleTechnical deep-dives into malware analysis, bug bounty write-ups, and zero-day research findings.
 #WORDPRESS
#WORDPRESS Diagnosing a WordPress site compromise that was redirecting visitors to adult content and pharmaceutical spam through injected malicious scripts.
Read Article #GOLANG
#GOLANG Hookd - A simple webhook server for testing and debugging.
Read Article #MONITORING
#MONITORING Setting up simple monitoring for your services.
Read Article #WEB3
#WEB3 Testing smart contracts using Remix IDE.
Read Article #WEB3
#WEB3  #WEB3
#WEB3 Solving The Rewarder challenge from Damn Vulnerable DeFi.
Read Article #WEB3
#WEB3 Solving the Side Entrance challenge from Damn Vulnerable DeFi.
Read Article #WEB3
#WEB3 Solving the Truster challenge from Damn Vulnerable DeFi.
Read Article #WEB3
#WEB3 Solving the Naive Receiver challenge from Damn Vulnerable DeFi.
Read Article #SECURITY
#SECURITY Setting up a collaborative code auditing environment using code-server.
Read Article #WEB3
#WEB3 Solving the Unstoppable challenge from Damn Vulnerable DeFi.
Read Article #BUGBOUNTY
#BUGBOUNTY Extracting and monitoring bug bounty scopes automatically.
Read Article #BLOGGING
#BLOGGING My journey through various blogging platforms over seven years and why I finally settled on Hugo with GitHub Pages.
Read Article #BUGBOUNTY
#BUGBOUNTY Comparing subdomain bruteforce and permutation techniques using Regulator, DNSGen, and AlterX to find the most effective reconnaissance strategy.
Read Article #BUGBOUNTY
#BUGBOUNTY Exploiting command injection through Ruby string interpolation in a Rails application to achieve RCE via DNS exfiltration.
Read Article #BUGBOUNTY
#BUGBOUNTY Comparing Amass, DNSX, and PureDNS for DNS resolution accuracy and performance in bug bounty reconnaissance.
Read Article #BUGBOUNTY
#BUGBOUNTY How trusting my instincts led to discovering a critical RCE that everyone else missed on a popular bug bounty program.
Read Article #BUGBOUNTY
#BUGBOUNTY A complete Docker-based infrastructure for bug bounty hunting featuring Traefik, XSS-Catcher, Rengine, and more.
Read Article #BUGBOUNTY
#BUGBOUNTY How I discovered my first RCE through basic reconnaissance and exploiting a known Java deserialization vulnerability in Adobe ColdFusion.
Read Article #BUGBOUNTY
#BUGBOUNTY Exploiting a Server-Side Request Forgery vulnerability through WKHTMLTOPDF to access AWS metadata and local files.
Read Article #BUGBOUNTY
#BUGBOUNTY Exploiting a blind Out-of-Band XXE vulnerability to exfiltrate sensitive data despite misleading error messages.
Read Article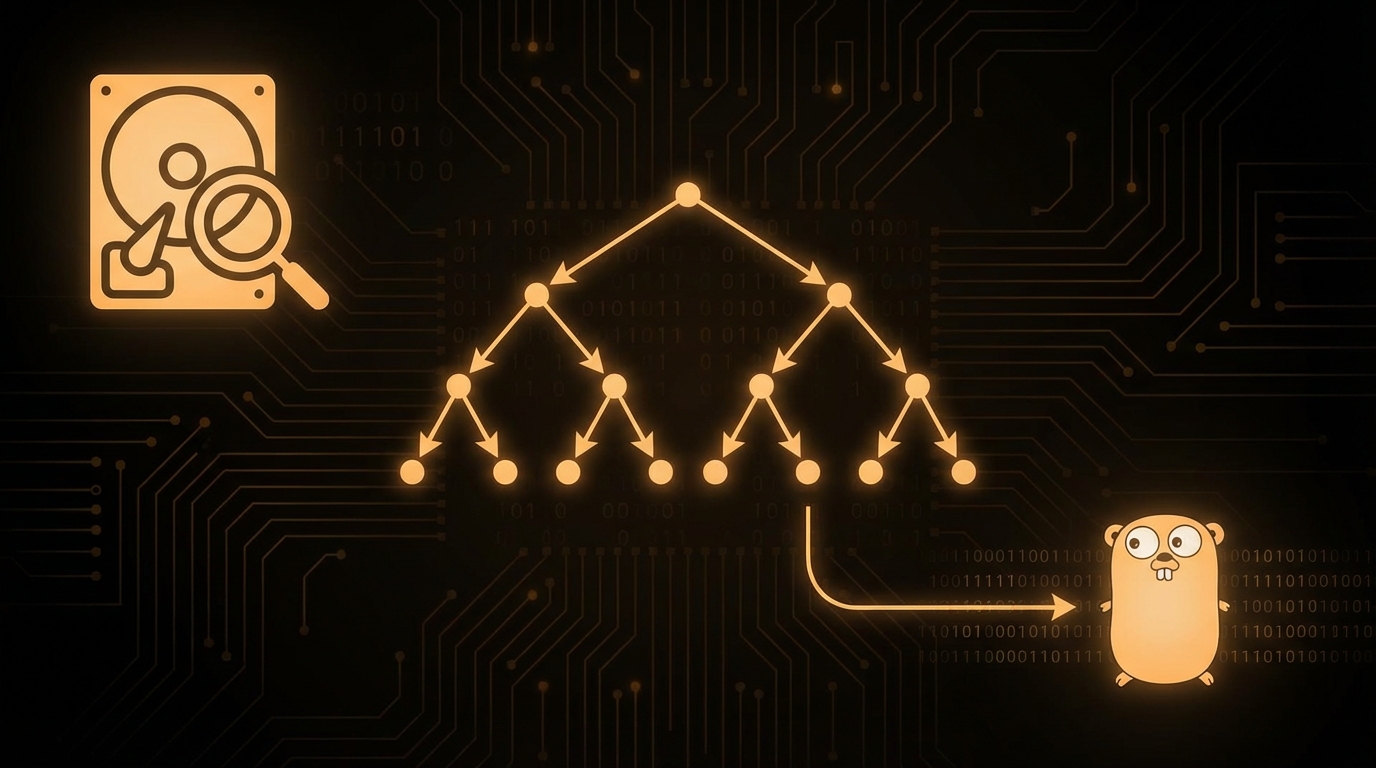 #GOLANG
#GOLANG Implementing binary search in Go to efficiently search through a 550 million line file in seconds instead of hours.
Read Article